Online Scams - What You Need To Know

The internet can be a blessing for most of us. Still, there are some with malicious intent who threaten to ruin its usefulness by trying to scam unsuspecting online victims.
"Smart people get scammed." This is the first chapter in Frank Abagnale's book, "Scam Me If You Can," and the best place for me to begin. If you're like most, you probably think it will never happen to you. You might be thinking, "I wouldn't fall for something so obvious," or perhaps you have put measures into place that will prevent it. You may have a fantastic, undecipherable, complex password, and you never, ever click on links in emails from strangers. Ok, I'll give you points for that; you're off to a great start.
But do you click on links in emails from someone you know? Do you love playing those quiz games everyone posts on Facebook (I'm guilty!). Do you shop online?
So let's talk about online scams, how you can minimize the risk of being deceived, and what you should do if you think you've been scammed or defrauded.
With the popularity of online shopping, cybersecurity has become essential to everyone. Shopping, even in the real world, involves money, and where there is money, there will be criminals. And with all this shopping in cyberspace, criminals lost no time in following the money trail targeting online shoppers, and fraudulently obtaining the information they can use for their financial gains. The three most common ways criminals attack online shoppers are:
- Unprotected computers
- Fake sites and email messages
- Charities
Online shopping brings us the best of two worlds: bargains and convenience. The internet can be a blessing for most of us. But fall victim to a scam, and it becomes a nightmare. I put together a list of the most common type of scams you need to keep an eye on, but this list is only the tip of the iceberg, as new scams pop up every day.
Phishing
Phishing mostly involves the sending of an email falsely claiming to be from an established legitimate enterprise, attempting to scam the user into providing sensitive information needed for their nefarious actions. The email directs the user to visit a Web site where they are asked to update personal information, such as passwords and credit card, social security number, and bank account numbers like the one below.
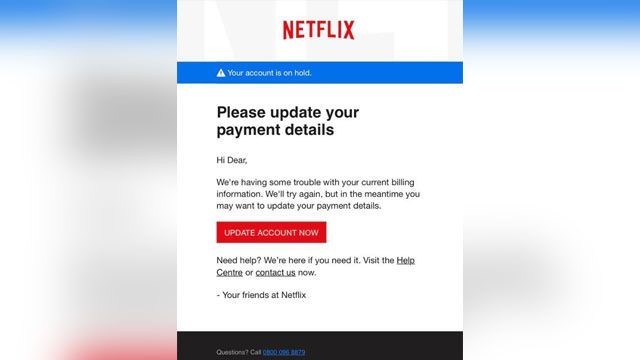
It might also try to get you to download a virus that infects your computer with malware or opens up a back door so they can steal sensitive data. Phishing happens most often via email, but it can also occur over the phone, via text, and on social media.
In particular, beware of online quizzes on social media. They will often try to get information by asking you common questions so they can then guess your passwords. Many people base their passwords on birthdays, children and pet names, and so on. My take-away here? If you use complex, random passwords that do not contain any personal information, you can enjoy the quizzes and discovering what Disney princess or villain you should be! Small plug here – you can learn more about passwords in my new e-course, Cybersecurity At Home, coming out this month.
Nigerian Prince
Believe it or not, this scam still works. It usually involves an email from a desperate Nigerian prince, asking for help in getting a large amount of money from the bank. Those who get hooked pay small amounts to get paperwork for the transaction and then finally get the money. However, all they are doing is putting money in someone else's bank account, and possibly even revealing their sensitive financial information.
Lottery or Contest Scams
These have also been around for some time and still fool people. The email tells you that you are a winner and need to pay a small fee to get your cash or prize.
Free Trial Offers
Free trials are often fronts for stealing your sensitive information, as well as many end up hitting your account with renewals each month if you are not careful. Check your financial accounts regarding autopayment settings and delete repeat payments as needed.
Ransomware
Ransomware is a very dangerous scam that is hard to overcome. The ransomware locks your computer until you pay the attackers in bitcoin. The longer you wait to pay, the more money they add on to the ransom. So far, even top computer security pros have not been able to restore data or track down the criminals. Note that if you have a backup hard drive connected to your computer, the ransomware can also lock that up. Back up all your data in a reliable cloud storage system and avoid clicking on anything that does not look legitimate.
Red Flags
 Look carefully at the website. If the spelling and grammar are not correct and the whole site looks like it was tossed together without thought, you should probably find another website to do your shopping.
Look carefully at the website. If the spelling and grammar are not correct and the whole site looks like it was tossed together without thought, you should probably find another website to do your shopping.
 Attackers will try to replicate brand-name sites. You could end up with knockoffs from China, or you might have your identity stolen. Knockoffs cost companies almost one trillion dollars annually. Check out the sites you shop at carefully to ensure they are real.
Attackers will try to replicate brand-name sites. You could end up with knockoffs from China, or you might have your identity stolen. Knockoffs cost companies almost one trillion dollars annually. Check out the sites you shop at carefully to ensure they are real.
 Additionally, look for the lock symbol on the address bar or https://. Most scam sites will not bother with getting an SSL certificate.
Additionally, look for the lock symbol on the address bar or https://. Most scam sites will not bother with getting an SSL certificate.
 Be leary of sites that continuously offer huge discounts. Bargains are more than likely knockoffs or lures to spend money without the goods being delivered. Compare prices at Google Shopping and shop around. Avoid the bargain basement.
Be leary of sites that continuously offer huge discounts. Bargains are more than likely knockoffs or lures to spend money without the goods being delivered. Compare prices at Google Shopping and shop around. Avoid the bargain basement.
 Beware of any site that requires you to pay only by wire transfer, pre-paid gift cards, bitcoin, or other cryptocurrencies. These are usually scam sites. My advice? If you stumble onto one of these, close the tab and move on.
Beware of any site that requires you to pay only by wire transfer, pre-paid gift cards, bitcoin, or other cryptocurrencies. These are usually scam sites. My advice? If you stumble onto one of these, close the tab and move on.
 Google the physical mailing address, see a map and get a Google satellite image of it. If the address does not exist, or the building looks suspicious, don't shop at that site. is not legitimate.
Google the physical mailing address, see a map and get a Google satellite image of it. If the address does not exist, or the building looks suspicious, don't shop at that site. is not legitimate.
 Read the reviews. Type in the name of the site or the product you are considering buying, and then add the word "scam." Take seriously all the feedback you find before doing business with that site.
Read the reviews. Type in the name of the site or the product you are considering buying, and then add the word "scam." Take seriously all the feedback you find before doing business with that site.
Can I Prevent It?
There are several things you can do to minimize the risk of being defrauded online. A little bit of vigilance and common sense can go a long way towards keeping you safe. Here are some do's and don'ts.
Do Protect Your Identity at All Costs
Do Shop only at reputable sites. Keep your passwords secure and change them regularly.
Don't Click on Links in Emails
Do be especially vigilant if the email claims to come from your bank or a sender you don't know.
Do Use Antivirus Software and Keep It Up to Date
Don't Store Credit Card Information at ECommerce Sites
Don't Shop at Overseas Sites
Do Use a Credit Card, PayPal, or Amazon Pay to Pay, not Debit Card or Check.
What To Do If You Are A Victim
No one wants to think about what to do if they are the victim of online fraud, but being familiar with the most important steps to take could help the whole incident become a lot less devastating.
✓ File a non-urgent incident report with your Police Precinct
✓ Report it to the FTC at https://ftccomplaintassistant.gov. If you received a phishing email, you could forward it to the Anti-Phishing Working Group at reportphishing@apwg.org. If you received a phishing text message, forward it to SPAM (7726).
✓ Notify the bank and credit card company and freeze your accounts by reporting the status of the cards as lost, stolen, or your statement as showing fraudulent charges.
✓ Contact the three main credit reporting bureaus, Equifax, Experian, and TransUnion, to file a Fraud Victim Statement. Also, ask them to issue a security freeze on your credit report so that no one will be able to try to get extended credit using your credit history and score.
✓ Deal with identity theft proactively by formulating an action plan for recovery at https://www.identitytheft.gov.
You can never be 100% safe online, but these guidelines will help minimize the risk of fraud.
One final thought, keep yourself informed. Sign up for free scam alerts from the FTC. The Federal Trade Commission in the US keeps a watchful eye out for the latest scams and posts them here: https://www.consumer.ftc.gov/features/scam-alerts