Cyber Risks Business Owners Ignore Until It’s Too Late

You Can’t Fix What You Don’t See:
The Cyber Risks Business Owners Ignore Until It’s Too Late

Most cybersecurity issues don’t start with hackers. They start with assumptions.
“I’m too small to be a target.”
“I don’t handle sensitive data.”
“I’ll deal with that later.”
These thoughts are widespread — especially among small business owners who are already juggling clients, deadlines, and a hundred other priorities. And honestly? They make sense. Cybersecurity doesn’t feel urgent… until it suddenly is.
With Safer Internet Day landing in February, it’s a good time to pause and look at the quiet risks many businesses don’t notice — not because they’re careless, but because they’re busy.
Why Small Businesses Are Attractive Targets
There’s a persistent myth that cybercriminals only go after big companies. In reality, small businesses are often easier targets because:
- They rely heavily on email
- They use multiple tools that don’t always talk to each other
- They don’t have dedicated IT teams
- They assume they’re flying under the radar
It’s not personal. It’s practical.
And most breaches don’t happen through dramatic hacks — they happen through everyday actions.
The Problem Isn’t Neglect — It’s Visibility
Most business owners care deeply about their work, their clients, and their reputation. What often gets overlooked isn’t security itself, but how deeply it’s woven into everyday operations.
Cybersecurity isn’t just about firewalls and software updates. It’s about:
- How you manage email
- How you store files
- How you share access
- How decisions get made when you’re in a rush
If you can’t see where risk lives in your day-to-day workflow, you can’t fix it.
The “I’ll Circle Back to That” Trap
Good intentions don’t usually fail because people stop caring.
They fail because day-to-day business takes over.
Most business owners fully intend to improve their systems, tighten security, and clean up loose ends. But when client work ramps up, emails pile on, and decisions need to happen fast, urgent needs and daily fires take priority.
The things that don’t feel urgent — like updating passwords or reviewing access permissions — get pushed to the bottom of the list.
And then, “I’ll circle back to that” often turns into:
- Shared logins that never get changed
- Old tools that still have access to your data
- Personal devices used for business work without safeguards
The problem is that cybersecurity issues thrive in this space. They don’t need big gaps or dramatic mistakes. They slip in quietly, through postponed decisions and unchecked assumptions.
And the longer something stays on the “later” list, the easier it is to forget it was ever there.
Everyday Cyber Risks Hiding in Plain Sight
Let’s talk about a few common areas where risk tends to hide.
Email Overload
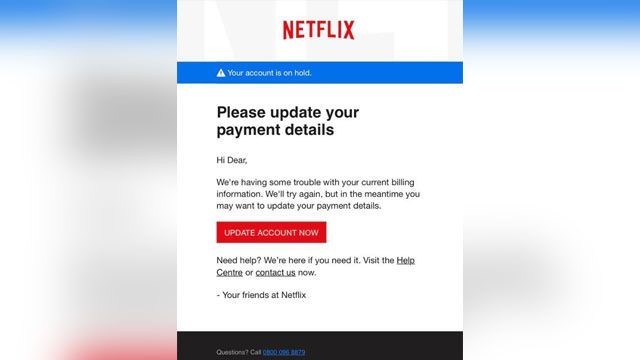
Busy inboxes are prime real estate for mistakes. Phishing emails don’t always look suspicious — especially when you’re scanning quickly between meetings.
One rushed click is often all it takes.
Password Fatigue
Using the same password across tools feels efficient… until it isn’t. Password reuse is one of the most common entry points for attackers.
File Sharing Shortcuts
Shared folders, old links, and outdated permissions are convenient — and often forgotten. Over time, access spreads far wider than intended.
Remote Work Habits
Working from home or on the go introduces new risks:
- Unsecured Wi-Fi
- Personal devices mixed with business work
- Lack of consistent security practices
Again, these aren’t mistakes. They’re side effects of modern business.
Why Awareness Matters More Than Fear
Fear-based messaging shuts people down.
Awareness opens doors.
When you understand where your real risks are:
- You make better decisions
- You build smarter habits
- You stop relying on assumptions
Safer Internet Day isn’t about panic. It’s about clarity.
Cybersecurity Is a Productivity Issue (Not a Tech One)
Here’s a reframe I want you to sit with:
Cybersecurity is part of productivity.
When systems aren’t secure:
- Work slows down during recovery
- Trust gets shaken
- Time gets pulled away from growth
Good security doesn’t add friction — it reduces it. It creates confidence. It protects momentum.
And most importantly, it allows you to focus on your actual work instead of reacting to preventable issues.
Small Changes That Make a Real Difference
You don’t need to overhaul everything to improve your security posture. Start with visibility.
Ask yourself:
- Who has access to what?
- What tools do I rely on daily?
- Where am I rushing instead of reviewing?
From there, even small steps help:
- Unique passwords
- Two-factor authentication
- Clear processes for handling data
- Knowing when to ask for help
Progress beats perfection every time.
Let me end this by saying, you don’t have to be the expert. One of the biggest misconceptions is that business owners need to understand everything about cybersecurity to stay safe.
You don’t.
You need the right guidance, the right systems, and the right support.
Cybersecurity doesn’t have to be scary, technical, or overwhelming. It just needs to be intentional.
Ready to Protect What Matters?
If you’ve been meaning to take a closer look at your digital security — or you’re realizing that “later” has been quietly stretching into “too long” — this is your sign.
Sometimes a simple conversation is enough to uncover:
- Hidden risks
- Easy wins
- Smarter ways to protect your business
If you’re ready to get clear and protect what matters, then click the button below to book time with me.
No fear tactics. No pressure. Just practical support.
Cyber Risks Business Owners Ignore Until It’s Too Late Read More »